Understanding the HIPAA Policies and Procedures
Today, I am diving a little deeper into the HIPAA Security Rules Administrative Safeguards, 45 CFR § 164.316 to break down the Policies and Procedures into byte-size portions to help you understand how they are significant to your organization. The standard requires regulated entities, Covered Entities (CEs) and their third-party vendors, to implement and maintain reasonable and appropriate written policies and procedures and documentation necessary to comply with the provisions of the Security Rule.
Specifically, it requires regulated entities to:
“Implement reasonable and appropriate policies and procedures to comply with the standards, implementation specifications, or other requirements of this subpart, taking into account those factors specified in § 164.306(b)(2)(i), (ii), (iii), and (iv) [the Security Standards: General Rules, Flexibility of Approach].
This standard is not to be construed to permit or excuse an action that violates any other standard, implementation specification, or other requirements of this subpart. Regulated entities may change their policies and procedures at any time, provided that the changes are documented and are implemented in accordance with this subpart.”
What is the Difference Between Policy and Procedure?
The Policies and Procedures requirement include:
Note: (R) = Required (A) = Addressable
- Policies and Procedures – 45 CFR 164.316(a)
- Documentation – 45 CFR 164.316(b)(1)
- Time Limit – (R)
- Availability – (R)
- Updates – (R)
The following table contains a list of possible Security Areas to Consider & Examples of Potential Security Measure:

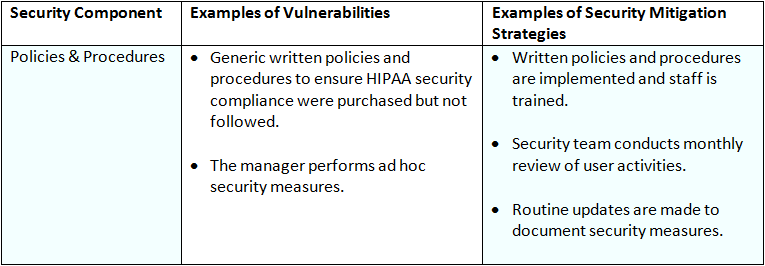
The following table contains a list of possible Security Components, Examples of Vulnerabilities, and Examples of Security Mitigation Strategies for the Organizational Safeguards.
Policies and Procedures
While this standard requires regulated entities to implement policies and procedures, the Security Rule does not define either “policy” or “procedure.” To help you understand the difference between the two I have included their Oxford Learner’s Dictionaries definition for both below.
Policy – a plan of action agreed or chosen by a political party, a business, etc.
Generally, policies define an organization’s approach. For example, most business policies establish measurable objectives and expectations for the workforce, assign responsibility for decision-making, and define enforcement and consequences for violations.
Procedure – a way of doing something, especially the usual or correct way.
Your policies and procedures (P & P’s) should reflect the mission and culture of your organization; thus, the Security Rule enables each regulated entity to use current standard business practices for policy development and implementation. P & P’s required by the Security Rule may be modified as necessary to meet the changing needs of the organization, as long as the changes are documented and implemented in accordance with the Security Rule.
The P & P’s standard is further explained and supported by the Documentation Requirement.
Documentation
The Documentation Requirement requires regulated entities to:
“(i) Maintain the policies and procedures implemented to comply with this subpart in written (which may be electronic) form; and (ii) if an action, activity or assessment is required by this subpart to be documented, maintain a written (which may be electronic) record of the action, activity, or assessment.”
A regulated entity must maintain, for a period of six years after the date of their creation or last effective date (whichever is later), written security policies and procedures and written records of required actions, activities, or assessments. A regulated entity must periodically review and update its documentation in response to environmental or organizational changes that affect the security of electronic protected health information (PHI).
Remember: Security is not a one-time project, but rather an on-going, dynamic process that will create new challenges as regulated entities organizations and technologies change.
Healthcare organization and third-party vendors should understand patients are entrusting them with their most private and intimate details, they do expect it to remain secure.

