HIPAA Security Rule Technical Safeguards
Today I am breaking down the Technical Safeguards of the HIPAA Security Rule, 45 CFR § 164.312, into byte-size portions to help you understand how they are significant to your organization. The HIPAA Security Rule establishes security standards for protecting all electronic protected health information (ePHI).
The Technical Safeguards require regulated entities and their third-party vendors, to implement measures to meet the security standards. These include things such as, implement access controls, audit controls, integrity, person or entity authentication, and transmission security requirements.
HIPAA Security Rule Technical Safeguards Definition
The HIPAA Security Rule defines Technical Safeguards as, 45 CFR § 164.304:
The technology and the policies and procedures for its use that protect ePHI and control access to it.
What are the HIPAA Security Rule Technical Safeguards?
Technical safeguards are becoming increasingly more important due to technology advancements in the health care industry. As technology improves, new security challenges emerge. Healthcare organizations face challenges every day in their effort to secure electronic PHI from various internal and external risks. To reduce risks to electronic PHI, regulated entities must implement Technical Safeguards. Implementation of the Technical Safeguards standards represent good business practices for technology and associated technical policies and procedures within a covered entity.
The Technical Safeguards and their implementation specifications are:
Note: (R) = Required (A) = Addressable
- Access Control – 45 CFR 164.312(a)(1)
- Unique User Identification – (R)
- Emergency Access Procedure – (R)
- Automatic Logoff – (A)
- Encryption and Decryption – (A)
- Audit Controls – 45 CFR 164.312(b)
- Integrity – 45 CFR 164.312(c)(1)
- Mechanism to Authenticate ePHI – (A)
- Person or Entity Authentication – 45 CFR 164.312(d)
- Transmission Security – 45 CFR 164.312(e)(1)
- Integrity Controls – (A)
- Encryption – (A)
Technical Safeguards Security Area to Consider
The following table contains a list of possible Security Components, Examples of Vulnerabilities and Examples of Security Mitigation Strategies for the Technical Safeguards.
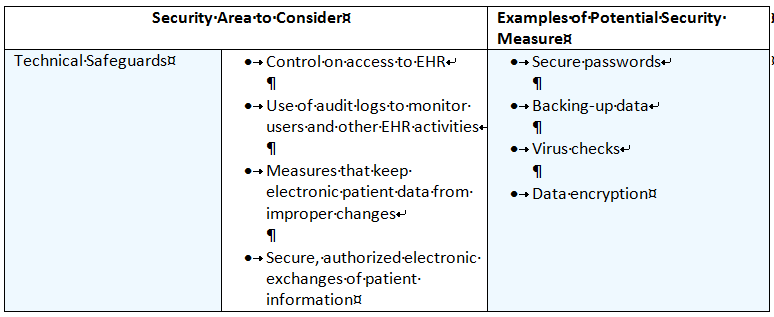
The Security Rule does not require specific technology solutions.
Determining which measure to implement is a decision regulated entities must make based on what is reasonable and appropriate for their specific organization, given their own unique characteristics, as specified in § 164.306(b) the Security Standards: General Rules, Flexibility of Approach.
Some solutions may be costly, especially for smaller regulated entities. While cost is one factor regulated entities may consider when deciding on the implementation of a particular security measure, it is not the only factor.
The Security Rule is clear that reasonable and appropriate security measures must be implemented, see 45 CFR 164.306(b), and that the General Requirements of § 164.306(a) must be met.
Together with reasonable and appropriate Administrative and Physical Safeguards, successful implementation of the Technical Safeguards standards will help ensure that regulated entities will protect the confidentiality, integrity and availability of ePHI.
Remember: Security is not a one-time project, but rather an on-going, dynamic process that will create new challenges as regulated entities organizations and technologies change.
Healthcare organizations and third-party vendors should understand that patients are entrusting them with their most private and intimate details, they do expect it to remain secure.

